
WordPress is a popular tool that helps many websites work. People all over the world work together to make it better. It has many small programs that make it easy for anyone to make a website, even if they’re not an expert.
But, like anything on the internet, there are bad people who try to harm websites. One big problem is something called malware.
That’s why it’s very important to know how to clean up malware from WordPress websites. If you can tell when identify when your WordPress site is infected with malware you can fix it quickly and stop it from happening again.
In this article, we’ll talk about why finding and fixing malware on your WordPress website is so important. We’ll explain how to do it, with or without special tools. We’ll also share tips to keep your website safe in the future. Finally, we’ll answer some common questions.
Bad software, called malware, can hurt your computer. It’s like a virus, worm, Trojan horse, or spyware. Even though WordPress tries hard to be safe, it can still be attacked by malware.
Malware can sneak into your WordPress site in different ways. The most common way is through bad plugins or themes. Sometimes, it can also come through weak spots in the main WordPress tool or other tools on your server.
When malware gets into a WordPress site, it can cause big problems. The person doing the bad stuff can delete files, put bad links in your writing, and even steal important info like passwords and credit card numbers. This can make your site stop working and make people not trust you.
Sometimes, you might not know that your site has malware unless you use a special tool to look for it. The longer you don’t know about the malware, the more harm it can do. That’s where good WordPress security tools like Delight IT Solutions come in. They can find and remove the bad stuff before it causes big problems.
If you’re looking for a good and free tool to check your WordPress site for bad stuff like malware, Delight IT Solutions is a great option. It checks your site all by itself for many problems, more than 28,700 of them, and gives you tips to make your WordPress site safer
The easiest and quickest way to find and remove bad stuff from WordPress websites is by using a tool called a plugin. Luckily, there are a few choices you can pick from.
We suggest using Jetpack Scan, which makes finding and removing bad stuff from WordPress automatic and easy. It saves you lots of time and effort. You can buy it by itself, but it’s even better when you get Jetpack’s bigger WordPress Security plan. This plan gives you lots of protection. Jetpack Scan goes beyond what Jetpack Protect does by quickly fixing bad stuff with just one click and also giving you a special wall that stops bad things from coming in.
The easiest and quickest way to find and remove bad stuff from WordPress websites is by using a tool called a plugin. Luckily, there are a few choices you can pick from.
We suggest using Jetpack Scan from Jetpack, which makes finding and removing bad stuff from WordPress automatic and easy. It saves you lots of time and effort. You can buy it by itself, but it’s even better when you get Jetpack’s bigger WordPress Security plan. This plan gives you lots of protection. Jetpack Scan goes beyond what Jetpack Protect does by quickly fixing bad stuff with just one click and also giving you a special wall that stops bad things from coming in.
First, if you haven’t done it yet, you need to put in the Jetpack tool and buy Jetpack Scan. After turning on the tool, you can scan your WordPress site for malware.
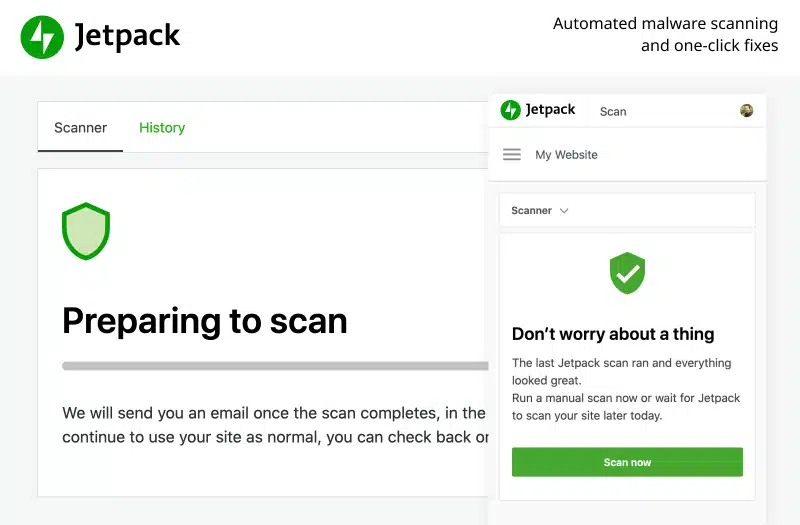
Jetpack will look for known bad things on your site. It won’t take long, just a few minutes
Best case, no bad stuff is found, and the scan says ‘No problems found.
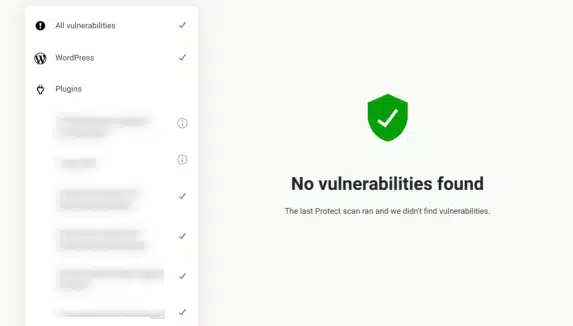
But if bad stuff is found, you’ll see a list of problems under ‘Bad Stuff Found.’ To get rid of it, just click ‘Remove Threat’ next to each one.
That’s it! The tool will clean up the bad stuff from WordPress for you. This won’t take long, just a few minutes
If Google thinks there’s bad stuff on your website, it might show a warning to stop people from going there. This is a big issue because most visitors won’t go past this warning.
So, after you’ve found and cleaned up the bad stuff on your site, the last thing to do is to get rid of these warnings. If Google marked your site, you can ask them to check again. Then you just have to wait for their answer.
This step is really important, so make sure you do it. Check our full guide on how to remove your WordPress site from Google’s blocklist. t.
The first thing you need to do is make your site temporarily unavailable. This means hiding your website stuff from visitors and showing them a message that says your site will be back soon.
You can do this using a tool called WP Maintenance Mode & Coming Soon.
It’s a free tool that helps you easily turn on the ‘site under construction’ mode in just a few clicks. After you add and turn it on, go to Settings → WP Maintenance Mode
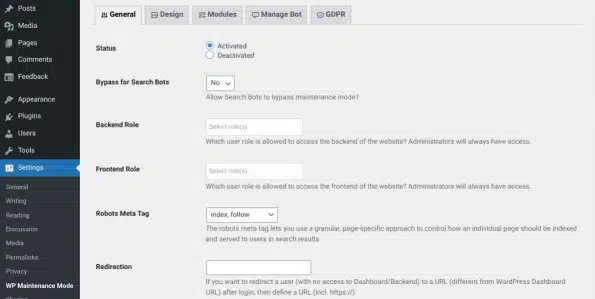
Then, choose ‘Activated‘ for the status. When you’re finished, click the ‘Save Settings‘ button at the bottom. Your site will now be in maintenance mode
It’s always smart to have a backup of your WordPress site , just in case something goes wrong or you accidentally remove something.
You need to back up two things: your database (where your content and settings are) and your files (like themes, plugins, and images).
The easiest way is to use a special tool called a WordPress backup plugin like Jetpack Backup. It helps you download your stuff whenever you want and also does automatic backups all the time. This means every change you make gets saved for later.
If you like doing things back up your WordPress site manually,using File Transfer Protocol (FTP) tools and phpMyAdmin. But this way is a bit more complicated and takes more time.
After getting your site ready, the next thing is to find any bad stuff. This means looking in your database, files, and the main code of your site.
One way to do this is by using a tool that finds bad stuff, like Malwarebytes
If you want to find bad stuff by yourself, you’ll need to carefully check different parts of your site. In your database, you can look for certain ways bad people write code (you can see examples in Step 9).
When checking your site’s main code for bad stuff, there are two main things to look for: ‘script’ and ‘iframe.’ If you see lines that start with ‘script=>’ or ‘iframe src=URL>’, and they have strange web addresses or file names, that’s usually a sign something’s wrong
If your WordPress is broken, a good way to fix it is by putting in new main WordPress files. You’ll only keep the wp-config.php file and wp-content folder.
First, get a new copy of WordPress from WordPress.org.
Open the file and delete the wp-config.php file and wp-content folder. Those are the only two things you should delete – everything else should stay.
After that, use your File Manager or FTP client to put the other files onto your server. This will replace your old files with the new ones. Learn how to bulk upload files via FTP.
It’s a good idea to check your wp-config.php file against the original one from WordPress Codex. This way, it’s easier to find anything that shouldn’t be there, like bad code.
Get a fresh copy of the wp-config.php file from WordPress Codex. Open this file and your current wp-config.php file in a text editor to compare them. Sometimes, your file might be a bit different, especially for your database info. But make sure to look for anything weird and remove it. Save the cleaned-up file and put it back on your server.
Next, you’ll want to put in a fresh copy of your WordPress design. But if you’re using a ‘child theme (a copy of your design with some changes), you don’t want to lose your work. So, you need to put in a clean version of your design while keeping your ‘child’ design.
On your WordPress dashboard, go to ‘Appearance’ → ‘Themes,’ then turn off your main design. After that, in your File Manager or FTP, delete your main design folder.
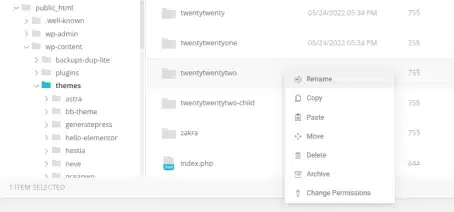
If you’re using a design from WordPress, go there, find your design, and get the newest version. If you’re using a special design or one from somewhere else, get the files for your design from that place. On your dashboard, go to ‘Appearance’ → ‘Themes,’ then choose ‘Add New’ → ‘Upload Theme
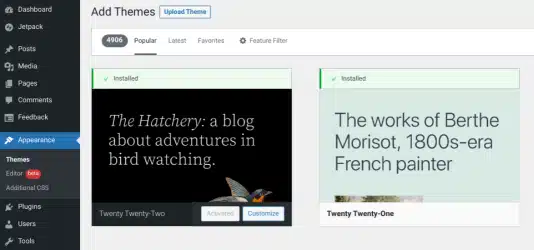
Choose the zipped file you recently downloaded. Once uploaded, click the ‘Activate‘ button.
Now, you can activate your child theme, and your site should be running the latest version of the parent theme, with all your customizations from the child theme intact.
The following step involves reviewing recently modified files. To achieve this manually, connect to your site using FTP or File Manager, then organize your files according to the ‘Last Modified‘ date column:
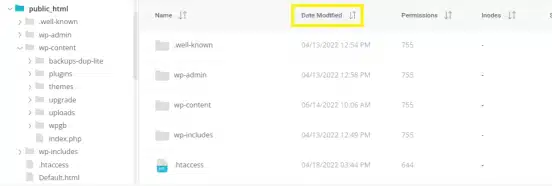
Take note of files that have been recently altered. Proceed to inspect each of them, examining the code for any suspicious additions. These may comprise PHP functions like str_rot13, gzuncompress, or eval.
If your WordPress site has fallen victim to malware, there’s a possibility that it has injected malicious content into your database tables.
To cleanse these tables, access your phpMyAdmin dashboard — typically provided by your hosting provider. Locate the database table that has been compromised and proceed to remove the malicious content. You can identify affected tables using a scanner tool such as Jetpack or by comparing your current files with the original ones.
Prior to making any changes, it’s crucial to create a backup of your site. You can access the original files from previous backups. Subsequently, search for commonly used functions (as outlined in the next step), suspicious links, and so on. If you discover any, manually delete the malicious content.
Once you’ve made the necessary changes, save them and test your website to ensure it’s functioning properly. If you prefer not to handle database modifications manually, you can use a tool like WP-Optimize. While not a dedicated malware removal plugin, it can clean and optimize your database. However, for a more comprehensive malware detection and removal solution, consider using a dedicated plugin like Jetpack Scan
When intruders manage to infiltrate your website, they often leave a concealed ‘backdoor’—a covert entry point for potential re-entry. These access points are typically disguised within files resembling your regular WordPress files but located in incorrect directory positions.
To unearth and eliminate these hidden backdoors in your WordPress site, a search through common files and folders is necessary. These include wp-content/plugins, wp-content/uploads, and wp-content/themes.
During the inspection of these files, it’s essential to watch for various PHP functions, such as:
While these functions themselves don’t inherently denote malicious behavior, their usage and context can sometimes hint at potential risks.
For instance, malicious PHP code is often:
Similar to database tables, we recommend comparing your current files with the original versions to ascertain if there’s a valid reason for the code’s presence.
It’s important to note that modifying WordPress files can disrupt critical functions of your site, so it’s advisable to proceed only if you possess experience in handling them. Alternatively, consider utilizing a plugin like Jetpack Scan or seek assistance from a professional.
Acquiring the knowledge to eradicate malware from WordPress websites is undeniably valuable. However, it’s even more beneficial to understand how to thwart malware from infiltrating your website in the initial stages. Let’s delve into actions you can implement for prevention
One of the fundamental strategies in preventing malware attacks on your WordPress site involves regular updates to your passwords and database credentials. Consistently changing these details significantly heightens the difficulty for potential hackers to gain unauthorized access to your site.
To modify your password, commence by logging into your WordPress dashboard and navigating to Users → Profile.
Within the Account Management section, opt for ‘Set New Password‘ to initiate the process
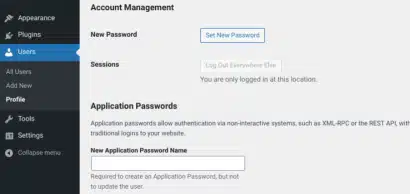
When you’ve completed the password change, click on ‘Update Profile‘ at the bottom of the screen. After modifying your password, it’s important to log out of all active sessions on your website, including any devices or browsers you may have used to access your WordPress site.
Regularly updating your WordPress database credentials is also crucial for enhancing security. To achieve this, navigate to the wp-config.php file, typically located in the root directory of your WordPress installation. You can access this file using FTP or File Manager.
Once you’ve opened wp-config.php, look for the following lines:
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'database_name_here' );
/** MySQL database username */
define( 'DB_USER', 'username_here' );
/** MySQL database password */
define( 'DB_PASSWORD', 'password_here' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );Make sure to replace the existing DB_NAME, DB_USER, and DB_PASSWORD values with the updated ones. After making these changes, save the file and close it.
To ensure the updated values function correctly, make corresponding updates on your server to match them. You can accomplish this by accessing your phpMyAdmin account, logging in, navigating to your database, and selecting the Edit option within the users table
One of the primary methods hackers utilize to infiltrate WordPress sites is through outdated software. Thus, to mitigate the risk of malware attacks, it’s crucial to maintain an up-to-date website. This practice is key to ensuring your site incorporates the latest security enhancements and fixes.
To update the WordPress core, access your dashboard and click on the Updates section. If a newer version of WordPress is accessible, a notification will appear at the top of your screen.
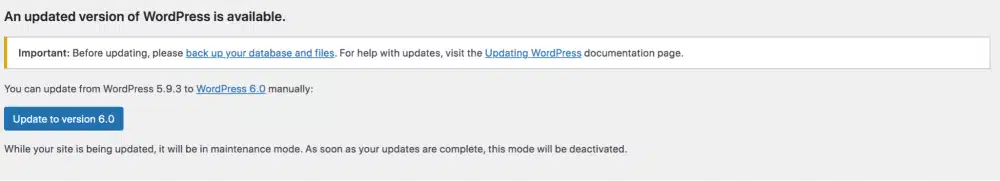
To update to the latest version, simply click on the Update button.
Ensuring your plugins and themes are up to date is equally critical, as developers frequently release security updates for them.
Access your WordPress site, and go to the Updates tab to check for available plugin or theme updates, which are displayed alongside the main WordPress version updates.
Select the Update Plugins or Update Themes button to install the most recent versions. If you prefer automation, consider using Jetpack’s Automatic Plugin Updates feature. This feature will automatically install new versions of WordPress, plugins, and themes as soon as they’re released.
To activate this feature, you’ll need to install and activate the Jetpack plugin. Once connected to your WordPress.com account, navigate to Jetpack → Settings → Writing.
Scroll down to the Automated Updates section at the bottom of the page and choose the types of updates you wish to enable: WordPress Core Updates, Plugin Updates, and/or Theme Updates.
Be sure to save your changes once you’ve made your selections. You can also manage updates on your Activity Log page and run them all at once by selecting the Update All button
You should also regularly scan your WordPress site for malware using a plugin like Jetpack Scan. Jetpack Scan will review your site for known malware and send you an email if they find anything wrong.
Once you download and install the plugin on your site, you can access the malware scan tool by clicking on Jetpack → Backup & Scan in the WordPress dashboard. There, you can see the current status of your site, and run a new scan if you’d like.
To enhance the security of your WordPress site and guard against malware attacks, we recommend installing an automated backup plugin such as Jetpack Backup
Jetpack Backup stands out as the top best WordPress backup plugin due to its real-time website saving capabilities. Any changes made, be it updating a page, publishing a post, or completing a purchase, are instantly reflected in the latest backup file. This integration seamlessly complements Jetpack Scan.
In the event that malware is detected on your site, Jetpack Scan promptly notifies you. From there, you can swiftly restore a backup from just before the security breach occurred — a process easily executed even from your mobile device while on the move. This means you can bypass the intricate steps of malware removal outlined earlier.
Now that we’ve covered WordPress malware detection and removal thoroughly, let’s conclude with some frequently asked questions to ensure we’ve addressed the key areas.
What are the indicators of a WordPress malware infection?
Detecting a malware infection on your WordPress site involves observing several signs. Initially, you might notice a slowdown in site loading or encounter error messages. Subsequently, unexpected new users or files may appear on your site. Lastly, your website may end up on Google’s blocklist or be flagged by visitors’ antivirus software. If any of these signs manifest, prompt action is crucial to clean up your WordPress site. Neglecting a malware infection can result in significant consequences, such as data loss and website downtime.
How does malware typically infiltrate a WordPress site?
Malware can infiltrate a WordPress site through various avenues. It often exploits vulnerabilities in WordPress plugins or themes. Additionally, hackers may upload malware after gaining access to your site through insecure passwords or other means.
Can I handle WordPress malware removal myself?
While you have the option to engage an external entity to remove malware from your site, this route can be quite costly. Alternatively, you can identify and eliminate malware from WordPress by utilizing a plugin like Jetpack Protect. This solution is efficient, user-friendly, and reputable.
For those with experience in web development, manual removal of WordPress malware is possible. However, this process is meticulous and carries the risk of causing significant errors on your site. Proceed with caution if you choose this option
WordPress, known for its flexibility and robustness as a CMS, is also a prime target for hackers due to its widespread use. Among the major threats faced by WordPress websites, malware stands out prominently.
As outlined in this post, we’ve discussed multiple approaches to identify and eradicate malware within the WordPress environment. The quickest and simplest method involves utilizing plugins like Jetpack. Conversely, manual malware removal is an option. Additionally, we emphasize the importance of regularly updating your WordPress software and maintaining backups to mitigate potential issues in the future.
If you seek a hands-off and reliable approach to automatically monitor your site for malware and vulnerabilities, consider giving the free Jetpack Protect plugin a try.
Looking for more comprehensive security features, such as one-click malware removal and an array of security capabilities including site backups? Explore Jetpack Security and fortify your website today!